Anyone who has interacted online with others through comment sections, social media posts, or discussion forums is probably familiar with spambots. These annoying automated computer programs generate unwanted, unrelated comments that are sprinkled among legitimate ones in an effort to sell products or services or attract clicks that can spread scams or malware.
In fact, according to Security Today, more than 30% of all internet traffic is generated by malicious bots.
Today, we’re going to learn about spambots, how they work, common types of spambots used, signs of spambot activity, and how to stop them. Finally, we’ll see how Akismet’s top‑rated AI‑driven anti‑spam solution is successfully leading the charge of blocking spambots on the internet.
What is a spambot?
A spambot is a computerized program that repetitively sends spam throughout the internet. It is often used to post irrelevant messages in places where people interact with one another, including comment sections of websites, social media messaging platforms, or online discussion forums.
How do spambots work?
Most spambots begin their nefarious activity by automatically setting up fake accounts on social media, email hosts, or forums, which typically only require basic information such as a name and email address.
Once spambots gain access to their target websites, they can begin posting spam messages based on a specific set of rules. Email spambots might scan, scrape, and save email addresses or phone numbers on the web to fuel future spam activities.
What are common types of spam caused by spambots?
Spambots can be extremely agile and used in a wide variety of places on a website. Here are a few of the most common ways you might encounter spambots:
- Contact form spam. spambots can be programmed to automatically fill out contact forms online. This allows them to gain access to a particular website or admin who receives the form submissions. Sophisticated bots may be able to implement SQL injection attacks as well.
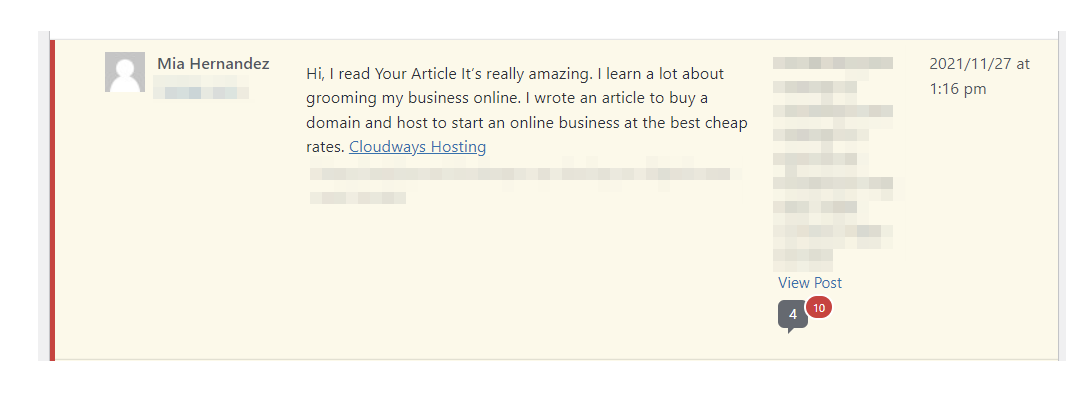
- Comment spam. Many websites offer comment sections where users can post questions, share ideas, or express opinions. spambots may automatically insert a spam comment in these areas, advertising unwanted products or services or tempting users to interact with them. The malicious actors can then cause those users to fall for scams or insert malware onto their devices.
- Fake account registrations. Imposter accounts can be automatically generated, especially if websites ask for only a few basic pieces of information like a name and email address. These accounts allow spambots to gain access to websites for future spamming activities such as posting negative reviews or wasting the time of a sales team focused on non‑existent customers.
- Forum spam. Online forums are great places for people to discuss just about anything they are interested in. spambots pollute these spaces by posting unrelated information among legitimate comments and discussions. Forums that allow anonymous posting can be especially vulnerable.
- Email spam. Gaining access to a large number of email addresses can fuel spam activity. Some spambots can scrape the web, access email lists, and save them to a database, which can then be used by cybercriminals to spread malware, run phishing attacks, or set up future scams.
- Doxxing. Doxxing occurs when spambots maliciously publish private information on a public forum. This may include publishing financial details or posting private data that could put people in potential physical harm.
What are the motivations behind spambots?
Do you ever wonder why cybercriminals spend time creating spambots and what their ultimate purpose could be? The motivations behind spambots are varied and numerous. Here are a few of the most popular reasons for creating spambots:
- SEO manipulation. Some spambots attempt to trick Google’s algorithms into believing that a particular website deserves top ranking by adding backlinks from other sites
- Phishing. Other spambots work to promote phishing scams, hoping that users will give up key account information such as passwords or usernames. These spambots may attempt to gain access to credit card or other financial information.
- Malware distribution. spambots may also be used to distribute malware through the continued sharing of tempting links in comment threads.
- Social media manipulation. Like trying to trick Google Analytics, spambots may be used to manipulate social media activity as well. Spam comments or posts may attempt to sway public opinion or create an illusion that something is more widespread and popular than it actually is.
- Advertising and promotion. Finally, spambots may be used to promote products and services, adult content, or too‑good‑to‑be‑true offers in an attempt to attract user interaction.
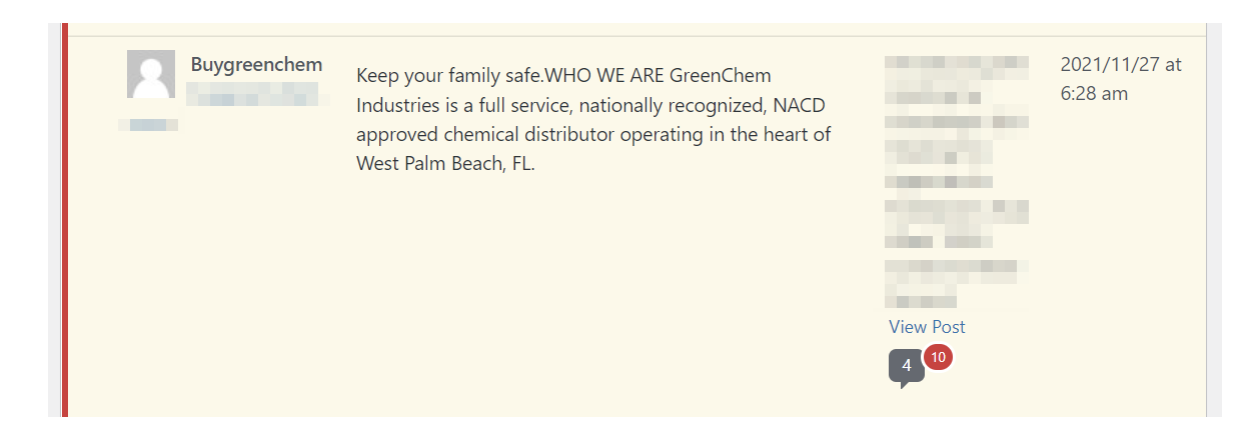
What are common signs of spambot activity?
In order to stop spambot activity, it’s important to understand common signs before unwanted posting gets out of hand and your user base is inundated with unwanted email or spam messages. Here are things to look for:
- A sudden surge in traffic. From a system perspective, if your IT department suddenly notes a rapid surge in traffic on your website, you may be a target for spambot activity.
- High bounce rates with short session durations. If you happen to see higher than normal bounce rates with very short session times, you may have spambots visiting your site.
- Inconsistent or patterned user behavior. spambots that are posting on website forums or in comment sections will display inconsistent and nonsensical user behavior. They won’t respond appropriately to other posts.
- Irrelevance. In most cases, spambots will post irrelevant advertisements, comments or questions in public forums that don’t follow the existing conversation. If they’re programmed to respond to others, the language used may also seem out of place.
- Activity from known malicious IP lists. If you keep a list of malicious IP addresses as part of your cybersecurity practices, you may be able to flag anything from the same IP address as potential spambot activities.
- Excessive errors. Many spambot messages contain a great deal of errors in terms of grammar or spelling. They may not even make sense at all.
- Ridiculous deals. If a product or service is advertised at prices that sound way too good to be true, they probably exist only to draw clicks to a malicious site or activate malware or phishing attempts.
- Pushing users to click or forward. spambots designed to spread malware or facilitate phishing attempts need users to click on links or forward them to others on their contact list. Urgent requests to do so should be a red flag for spambot activity.
- Unknown respondents. If activity is coming from individuals who seem suspicious, in combination with any of these other clues, you may be dealing with spambot activity.
What are the implications of not blocking spambots?
For a busy website manager or IT department, it can be tempting to ignore spambot activity, at least for the time being if other technical issues are pressing. spambot activity may be seen as merely annoying, but not as dangerous as other cybercriminal activity.
However, not blocking spambots can have far‑reaching consequences for your overall business. Here are a few to consider:
- A bad user experience. First and foremost, spambots can contribute to a negative user experience. If you are trying to encourage discussion, comments, and questions on a public forum, having random spambot postings throughout can be irritating and annoying to those trying to truly interact with one another.
- A tarnished site reputation. Not only can you develop a poor site reputation if spambot activity is regularly associated with your website, but some spambot activity may include posting fake negative reviews or the generation of false complaints, which can have negative implications for your business as a whole.
- The risk of penalties from search engines. Search engine algorithms are constantly being developed to deal with spambots and false optimization attempts. Your site could be penalized for carrying irrelevant links to other sites if they violate search engine rules.
- The risk of site blocklisting. If dangerous spam becomes a rampant problem on your site, search engines and web browsers may actually blocklist your site or display warnings to potential visitors. This could eliminate the majority of your site traffic in a matter of days.
- Reduced site performance. It takes time and server resources to process spambot activity. This may slow down the performance of your site for legitimate users.
- Increased server costs. Some server hosting companies charge based on the resources used. Unwanted spambot activity may increase these costs.
- A waste of time and money. If spambots operate by generating fake inquiries, your business could waste valuable sales force time trying to follow up or sort through junk leads to get to actual prospects.
How to stop spambots
The good news is that there are several tools and solutions to help you stop spambots effectively. Each has advantages and disadvantages, but all of them can help you eliminate unwanted posts, email scraping, and fake account set‑ups.
Akismet: The #1 AI‑powered anti‑spam solution
The top choice to stop spambots is Akismet, which is an AI‑powered anti‑spam solution used by more than 100 million websites today. It uses machine learning technology to identify and get rid of 99.99 percent of all spam.
What is Akismet?
Akismet is a powerful anti‑spam solution built on cutting edge artificial intelligence and machine learning technology. It has been blocking spam for nearly two decades, and its technology is continuously learning to stay ahead every step of the way. It’s successfully removed more than 500 billion pieces of spam across more than 100 million sites.
How does Akismet work?
Unlike some other spam blockers, Akismet works completely in the background, so your users experience zero friction on your site. They simply navigate to the areas, discussion boards, and contact forms they want and proceed without so much as a CAPTCHA or box to click.
However, spambots are detected with near‑perfect accuracy and are booted from the site or prevented from submitting forms. Depending on your settings, Akismet can even toss comments directly in the trash without you ever having to see them.
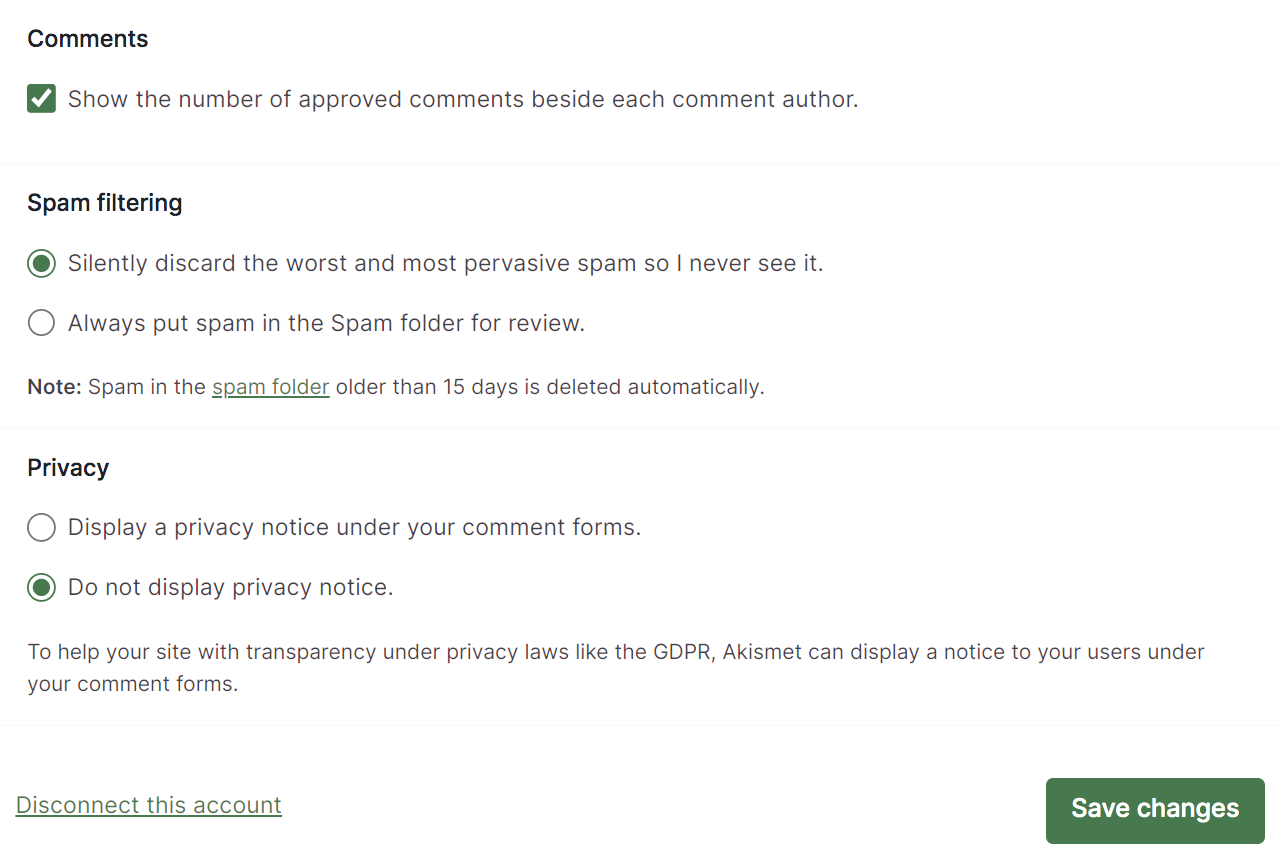
What are the benefits of using Akismet?
Sites that rely on Akismet reap many benefits. First, since Akismet works in the background without relying on your users to “prove” that they’re not spambots, the user experience is far superior to other prevention methods like CAPTCHA. A faster, less annoying user experience often results in better conversion rates and higher overall visitor satisfaction.
Second, since Akismet’s technology learns from every spam it’s removed from more than 100 million websites, you benefit from all this knowledge. Just about everything that’s known about spam is stored in a cloud-based database, ready to inform Askimet’s actions for your specific site. This learning will continue over time, keeping your site nearly free of all new spam — even new spam techniques that have yet to come!
Third, because the database is stored in the cloud, you get the benefits of Akismet without any negative effects on speed or storage for your site.
Want to know how it works in real life? Explore how ConvertKit is using Akismet to protect entrepreneurs from spam. In this case study, ConvertKit executives walk through their spam challenges, potential negative effects spam has on their business and the entrepreneurs they support, and how Akismet is helping them solve their spambot problem.

How to get started with Akismet
If you’re ready to eliminate spam without frustrating visitors, you can download the Akismet plugin for WordPress today. On another platform? Developing a unique app? Learn about the flexible Akismet API to integrate it with your project.
Enterprise companies can reach out to the Akismet team to get a custom solution just for them.
Honeypots and reCAPTCHA
Two other common ways that companies can stop spambots are honeypots and CAPTCHA puzzles.
Honeypots are set up like a trap, attempting to lure spambots to complete an invisible, unneeded field so that spam can be quickly identified. While real users do not see the invisible field, spambots are automatically scanning code for fields to complete and fall for the honeypot trap.
Although honeypots are effective at blocking spambots targeting form completion, they do not effectively stop email scraping or other types of spambot activity.
reCAPTCHA puzzles are familiar to nearly everyone, requiring that the user check certain boxes that contain specific images to prove that they’re human or complete other types of puzzles. CAPTCHA and reCAPTCHA puzzles are often frustrating because images can be difficult to decipher or even understand across cultures.
Although a wide variety of other CAPTCHA alternatives have been developed in an effort to address these issues, they all still require user interaction and can be impossible to complete for those with various impairments.
Since CAPTCHAs are often needed at key points in the customer journey — such as requesting a sales call or checkout points — they can create a negative user experience and significantly diminish conversion rates.
Web application firewalls (WAFs)
Traditional web application firewalls (WAFs) were created to guard against things like SQL injections, cross‑site scripting, and session hijacking. However, they often fail to keep up with the evolution of bad actors, including those using spambots.
While next‑generation firewalls (NGFW) tried to make headway in detecting new applications, they still use basic methods like simply blocking repetitive inquiries, identifying browsers, or blocking specific IP addresses. Many improvements rely on filters to identify malicious activity but are only somewhat effective at blocking threats. As bots advance, these NGFW also have trouble keeping up with more sophisticated activities.
In addition, businesses often struggle with managing WAF policies that can be operationally complex, leaving patches undone and resulting in an increased number of vulnerabilities.
IP blocking
Another proven method of stopping spambots is traditional IP blocking. Many IT departments have a list of IP addresses that have generated a great deal of malicious or spam activity in the past and can automatically block any traffic coming from those particular IP addresses.
Although generally effective, this approach does not prevent more sophisticated spambot activity and could potentially block activity from a legitimate source. It’s limited in overall effectiveness and more manual to set up and manage.
Confirmed opt‑in (COI) or double opt‑in (DOI)
Businesses can also use a confirmed opt‑in or a double opt‑in approach to stop spambots that are trying to sign up with fake email addresses. This process requires that new contacts be verified, requiring them to click on a link in an email sent immediately after they submit a form.
Although this process can be somewhat effective, screening out fake sign‑ups, it only addresses spambots that are setting up false accounts. Other malicious system activity or sophisticated spambots may go undetected.
In addition, the DOI process means extending the sign-up process. The more you require of prospects, the more likely some of them will abandon the sign-up process.
In addition, the younger generation often doesn’t check email as frequently as older generations, which causes a bottleneck in your engagement or purchase process. Finally, some users may not confirm and therefore slip through the cracks for future marketing outreach.
Multifactor authentication
A wide number of businesses now use multifactor authentication to provide an extra layer of security on their sites. This usually involves a user confirming their identity through more than one method, such as an email account or phone.
Although this can be very effective at ensuring that users are legitimate customers or prospects, it again adds another step in user engagement, potentially causing additional friction that can cause lost leads or abandonment of a checkout process.
Akismet: Leading the charge in blocking spambots
While many solutions exist to help businesses block spambot activity, it’s clear that the number one choice is Akismet. Its years of experience with blocking spam, coupled with powerful artificial intelligence and machine learning technology, make it the clear choice for a comprehensive, effective spambot blocking solution.
More than 100 million websites agree, taking advantage of the cumulative knowledge that Akismet has gathered since 2005. With 99.99 percent effectiveness and an impressive track record of removing more than 500 billion pieces of spam from the internet, it’s hard to argue about the solution’s success.
Most importantly, Akismet completes its job unbeknownst to your users and visitors. Prospects and customers can journey smoothly through your sales funnel without stopping to complete CAPTCHA puzzles or double opt‑in confirmations at inopportune times. This means a smoother engagement process and less friction, leading to happier users and a better reputation.
With its advanced technology and comprehensive spam database residing in the cloud, Akismet doesn’t affect processing time, server activity, or loading speeds. This ensures that your site continues to operate quickly and effectively without diverting resources to spambot detection and removal activities.
Finally, Akismet will continue learning into the future, which means that, even if spambot creators get more sophisticated, Akismet will be ready with a spambot blocking solution.
